Cybersecurity Services in North Florida
Your Business doesn’t get Hacked because an employee clicked on a link, its because your IT provider let You down
Don’t let the wrong cybersecurity company put your business at risk.

Your team is amazing. The customer service is always on point. I would have assumed you had 100+ [staff] just based on the high-quality customer service and fast response times. I feel like I’m your only client!
Kelly Pourciau, Jax Chamber

Start protecting your business today with cybersecurity services!
Get a free dark web scan.
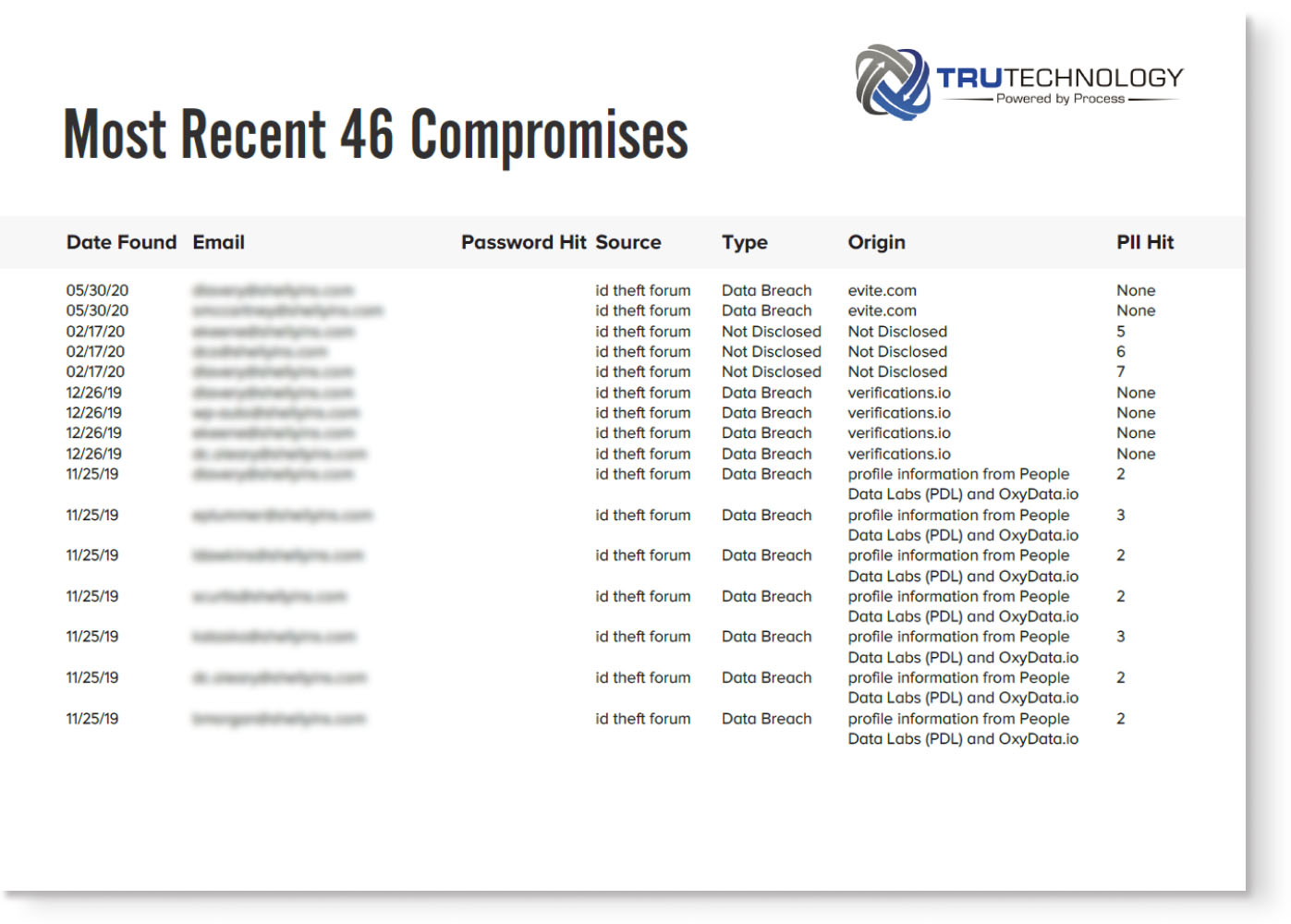
See a quick example below
We will contact you within 24 hours to report on findings
Prevent sensitive company information or customer data being hacked or stolen.

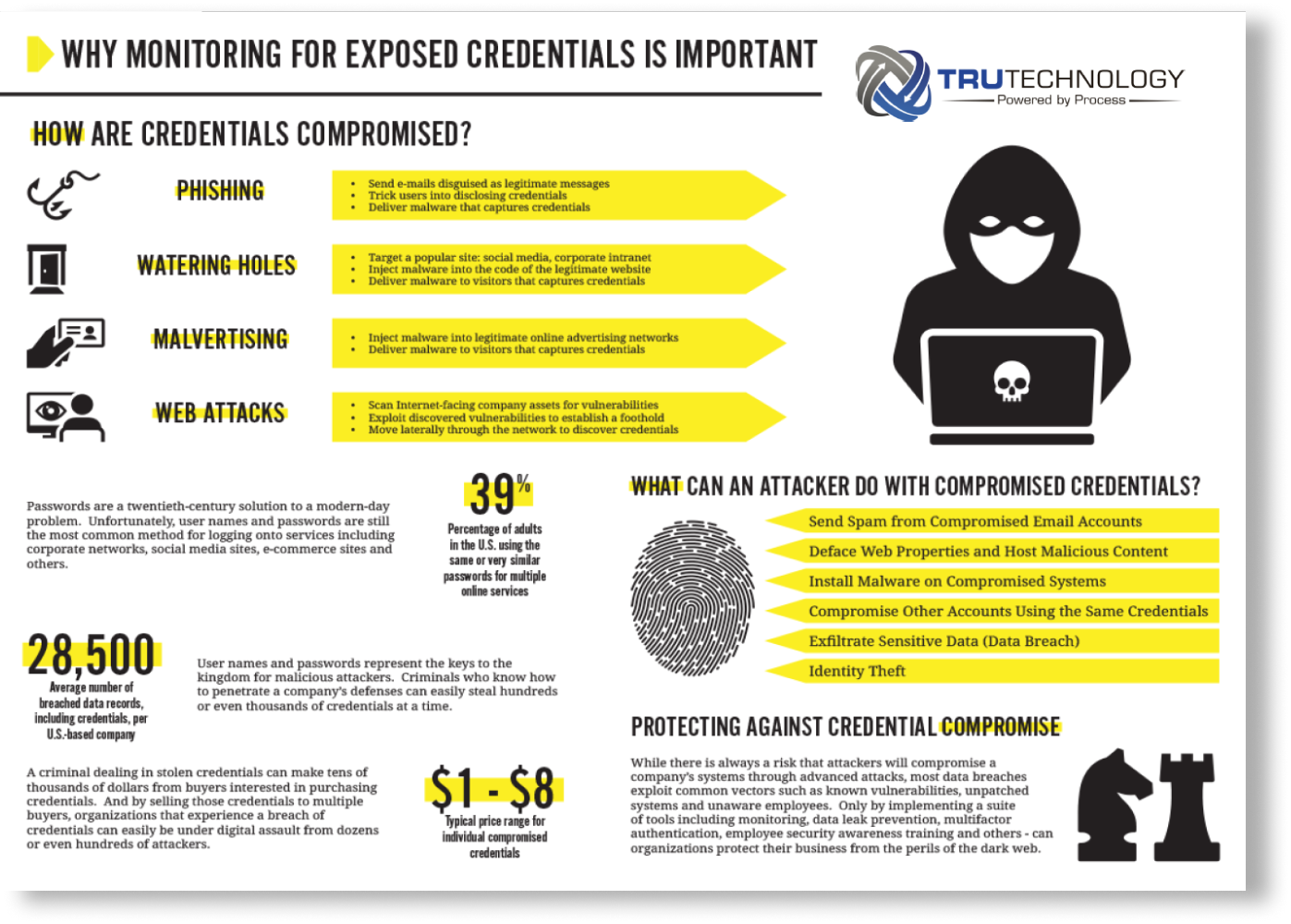

Hackers and cybercriminals launch attacks every 39 seconds,
which is an average of 2,244 times per day, with more than 8 Billion records confirmed to be compromised in the last year alone. Our unique approach ensures our cybersecurity services are done right so you can achieve piece of mind.
Get IT support services that really work.

The TRUTECHNOLOGY team
Reduce Risk
Receive protection like never before, reducing your risk of data breach (or worse)rse).
Align Your IT with Your Business Goals
Watch your technology and business work together to achieve success.
Increase Efficiency
Notice an immediate increase in your day-to-day efficiency.
Providing cybersecurity services to North Florida businesses for more than two decades.
We’re committed to giving you total peace of mind about your business’s technology. We’ll use our experience and expertise to not only solve your technology problems when they come up, but prevent them from occurring in the first place!
Request A Security Scan
FREQUENTLY ASKED QUESTIONS
WHAT IS THE DARK WEB?
The dark web is a hidden universe contained within the "Deep Web"- a sublayer of the Internet that is hidden from conventional search engines. Search engines like Google, BING and Yahoo only search .0.4% of the indexed or "surface" Internet. The other 99.96% of the Web consists of databases, private academic and government networks, and the Dark Web.
The Dark Web is estimated at 550 times larger than the surface Web and growing. Because you can operate anonymously, the Dark Web holds a wealth of stolen data and illegal activity.
HOW DOES DARK WEB ID HELP PROTECT MY ORGANIZATION?
Our service is designed to help both public and private sector organizations detect and mitigate cyber threats that leverage stolen email addresses and password. Dark Web ID leverages a combination of human and artificial intelligence that scours botnets, criminal chat rooms, blogs, Websites and bulletin boards, Peer to Peer networks, forums, private networks, and other black market sites 24/7, 365 days a year to identify stolen credentials and other personally identifiable information (PII).
HOW ARE THE STOLEN OR EXPOSED CREDENTIALS FOUND ON THE DARK WEB?
Dark Web ID focuses on cyber threats that are specific to our client's environments. We monitor the Dark Web and the criminal hacker underground for exposure of our client's credentials to malicious individuals.
We accomplish this by looking specifically for our client's top level email domains. When a credential is identified, we harvest it. While we harvest data from typical hacker sites like Pastebin, a lot of our data originates from sites that require credibility or a membership within the hacker community to enter. To that end, we monitor over 500 distinct Internet relay chatrooms (IRC) channels, 600,000 private Websites, 600 twitter feeds, and execute 10,000 refined queries daily.
DOES THE IDENTIFICATION OF MY ORGANIZATION'S EXPOSED CREDENTIALS MEAN WE ARE BEING TARGETED BY HACKERS?
While we can't say definitively that the data we've discovered has already been used to exploit your organization, the fact that we are able to identify this data should be very concerning. Organizations should consult their internal or external IT and/or security teams to determine if they have suffered a cyber incident or data breach.
